This week, Marks & Spencer, one of the UK’s most trusted high street retailers, found itself in the headlines for all the wrong reasons. A serious cyberattack, believed to have been launched by the infamous Scattered Spider Group, caused significant disruption across M&S’s operations. From frozen online orders to disrupted in-store services and a staggering £600 million wiped off its market value, the incident serves as a high-profile reminder of just how disruptive cybercrime can be.
But if a company like M&S (with world-class security resources) can be caught out, what does that mean for the rest of us?
The M&S breach: A quick summary
The attack, which began around 20th April, appears to have involved ransomware deployed via social engineering techniques. M&S was forced to shut down several core systems, affecting:
- Online orders: Clothing and homeware purchases were suspended.
- In-store operations: Contactless payments, gift card usage and product returns were all hit.
- Supply chains: Stock availability was impacted across some branches.
- Financial standing: Investor confidence took a knock, with M&S shares tumbling.
Critically, while there’s no current evidence of customer data loss, the situation remains under investigation.
Why this matters to SMEs
You might be thinking, “That’s awful for them, but we’re not M&S.” True, but that’s exactly the point.
Big businesses tend to recover from these events. They have the brand resilience, crisis PR teams, and (frankly) the cash reserves to bounce back. Most SMEs do not. In fact, the National Cyber Security Centre has regularly warned that small and medium-sized organisations are increasingly being targeted, precisely because attackers know they’re often underprepared.

What happened to M&S could just as easily happen to a 50-person consultancy, a medium sized Charity, a local law firm, or a growing manufacturer. And if ransomware locks you out of your systems, stops your invoicing, or exposes customer data, the results can be terminal.
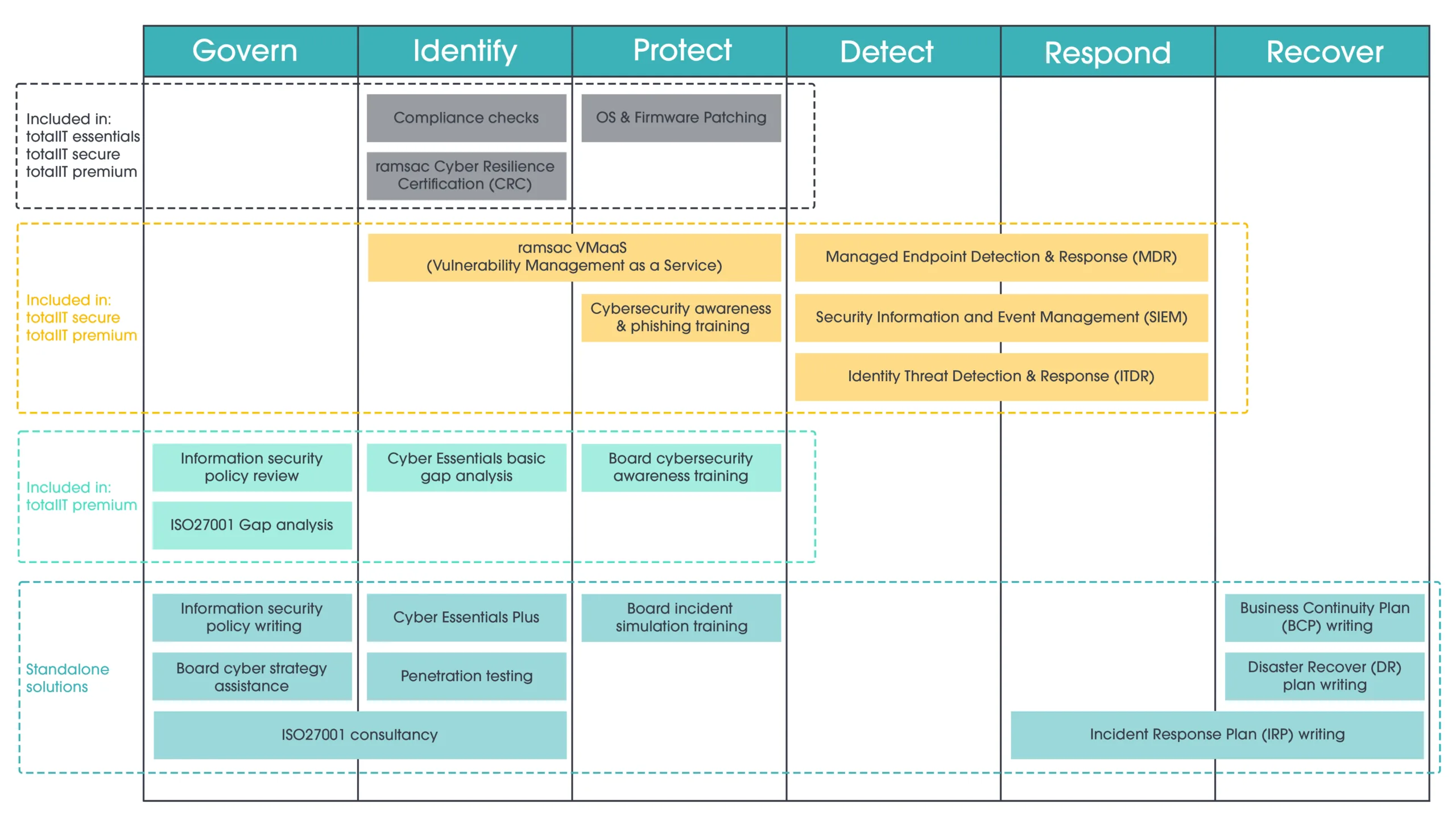
Key takeaways for SME leaders
Here are some tangible actions SMEs should take away from this incident:
1. 🔍Assume you are a target
Too many organisations still think, “Why would anyone hack us?” The answer is simple: because they can. Opportunistic attacks don’t discriminate – if your defences are weak, you’re fair game.
2. 🛡️Invest in layered security
Basic antivirus is no longer enough. SMEs should be deploying a multi-layered approach: secure endpoints, robust firewalls, phishing protection, and continuous monitoring.
3. 👥Train your people
Most breaches, including the M&S one, start with human error. Educate your team about phishing, suspicious links, and social engineering. Your people are your first line of defence.
4. 💾Backups are essential
Having fast, reliable, offline backups is your best insurance against ransomware. Test them regularly.
5. 📋Have a plan
If the worst happens, who do you call? What do you tell your clients? How do you keep operating? A well-documented incident response plan can be the difference between a hiccup and a full-blown crisis.
How ramsac can help
At ramsac, we specialise in helping SMEs build cyber resilience. Whether it’s a cyber audit, phishing simulation, or fully managed IT security, our mission is simple: to make IT simple and secure.
The M&S breach isn’t just a big business problem. It’s a wake-up call for all of us, especially SMEs, to double down on cyber hygiene.
If you’d like to discuss how your organisation can be better protected, we’re here to help.
Whitepaper – Cybersecurity threats facing UK SMEs in 2025
Discover the most pressing cyber threats facing UK SMEs in 2025 and learn how to protect your organisation with expert insights and practical guidance.