Picture this. You’ve invested in great software, you’ve got anti-virus tools running, and everyone in your team knows not to open suspicious emails (well… most of them). But there’s something missing. Something that ties it all together and makes your security setup more than a box-ticking exercise.
That missing piece? The perfect IT security policy.
What is an IT security policy… and why does it matter?
Think of your IT security policy as the rulebook for how your business protects its data, devices and systems. It sets out the do’s and don’ts for your team, clarifies responsibilities, and acts as your first line of defence when things go wrong.
A strong policy isn’t just there to keep your IT team happy. It’s your insurance against chaos. Without clear guidance in place, even the best intentions can lead to disaster. Ever had someone plug a USB stick they found in the car park into their work laptop? Or share a password in a team chat “just this once”? Without a policy that clearly outlines what’s acceptable, those “small” things can open the floodgates.
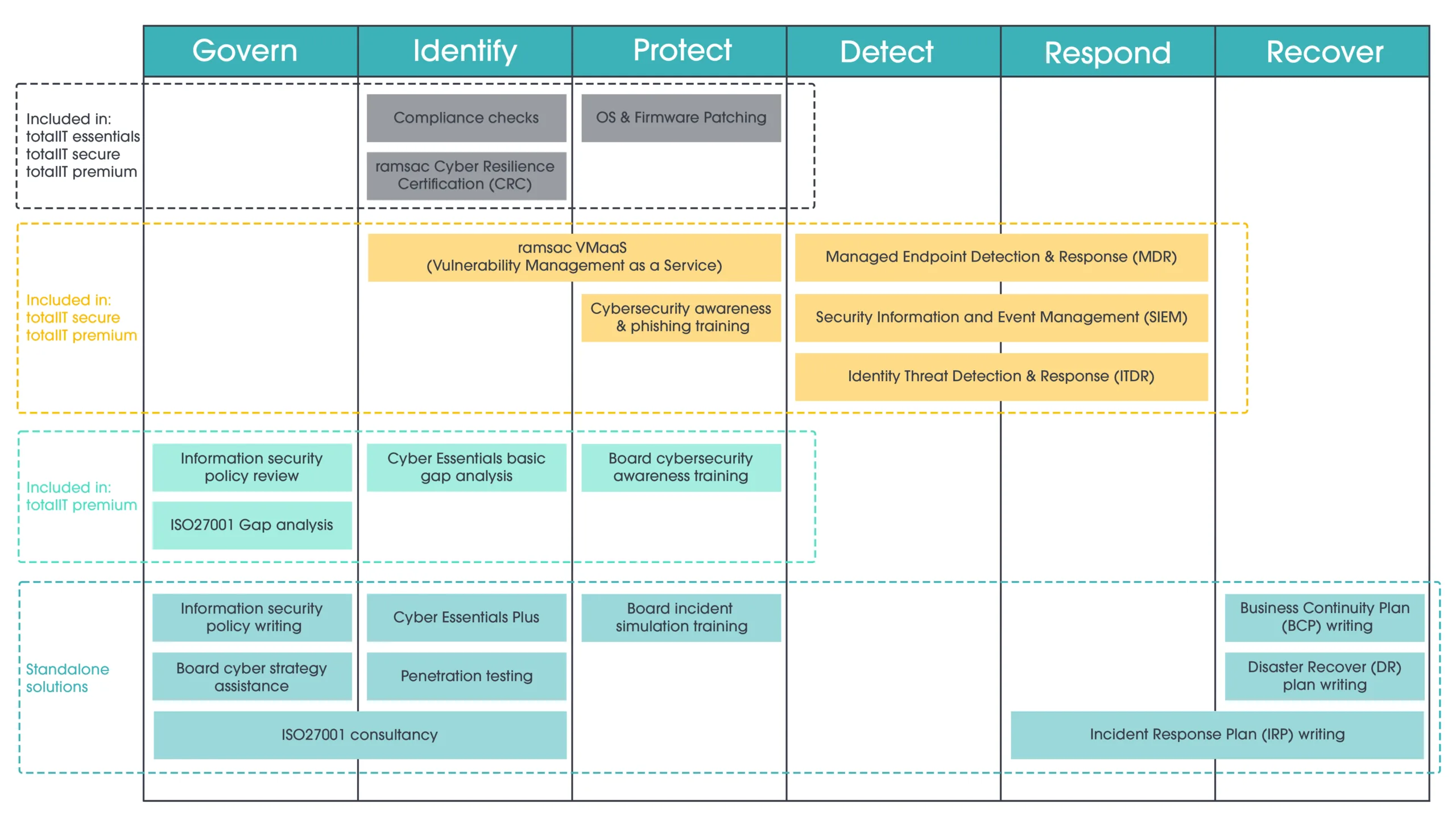
What does a good IT security policy include?
There’s no universal template that suits every organisation, but certain foundational elements should always be addressed.
Access control
Who can access what, and under what conditions, must be clearly defined. Your policy should outline how permissions are granted, reviewed, and revoked—especially for new starters, leavers, and role changes. It’s not just about convenience; it’s about ensuring only the right people have access to sensitive information.

Password management
Weak or reused passwords remain one of the most common causes of security breaches. Your policy should enforce the use of strong, unique passwords, promote the use of password managers, and support multi-factor authentication where possible.
Acceptable use
Staff need clarity on what constitutes appropriate behaviour when using company devices and systems. This includes rules around personal use, prohibited software, and the use of personal devices for work-related tasks.

Device security
Laptops, smartphones, and tablets must be encrypted, password-protected, and set to lock automatically. The policy should also include guidance on what to do if a device is lost or stolen—ideally with a clear escalation process.

Email and internet use
Staff should understand how to handle emails, particularly those with links or attachments from unknown sources. Guidelines should also be provided on browsing habits, the use of unsecured Wi-Fi networks, and reporting suspicious activity.
Incident response
No system is flawless. When incidents occur, your team must know what to do, who to notify, and what immediate steps to take. A strong policy sets out these expectations and supports a coordinated, timely response.
Data handling
Sensitive data—whether personal, financial or operational—must be handled with care. Your policy should include clear rules for storing, transmitting, and disposing of information securely, in line with data protection regulations.
Training and accountability
Even the best policy is ineffective without awareness. Staff should receive regular, role-appropriate training, and the consequences of non-compliance must be clearly documented and enforced.
A policy is not a static document. It should evolve as your organisation grows, your risks shift, and new threats emerge.
The risks of not having one
Let’s be honest, most data breaches don’t happen because of shadowy hackers breaking through firewalls like in a spy film. They happen because of everyday human errors. Reusing passwords. Leaving laptops unlocked. Falling for convincing phishing emails.
When there’s no agreed way of doing things, people do what’s quickest or easiest. That’s where the trouble starts. Without a security policy:
- Your staff might not know what to do in a cyber emergency
- You may not be compliant with legal or industry standards
- You leave yourself wide open to internal errors and external threats
Can you afford to rely on crossed fingers and good intentions?

So… where do you start?
If you’re thinking “we should probably have one of those” or “ours hasn’t been updated since dial-up internet was a thing”, you’re not alone. The truth is, creating the perfect IT security policy isn’t just about downloading a free template and hoping for the best.
What’s right for one business could be completely wrong for another. You need something tailored, clear, and practical, something your people will actually use and your IT team will be proud of.
That’s where ramsac comes in. We help organisations craft clear, effective IT security policies that reflect how they really work. We ask the right questions, highlight the gaps you may not have spotted, and make sure the end result keeps you protected and compliant.
Because your security policy should protect your business, not gather dust.
Is your organisation protected, or just hoping for the best?
If your IT security policy is out of date or incomplete, now is the time to take action. At ramsac, we specialise in creating tailored, practical policies that reflect how your business actually operates. Our experts will work closely with you to identify risks, clarify responsibilities, and implement a security framework that strengthens compliance and resilience.
Let’s start the conversation—because a good policy doesn’t just sit in a file, it protects your business every day.
Cyber Resilience health check from ramsac
Safeguarding your organisation against cyber threats has become increasingly vital, and assessing where you currently are is the first step to security. Find out which 10 questions you should be asking yourself about Cyber Resilience.