The only way to protect yourself from a threat is to know the threat that’s targeting you. This is essential for cybersecurity because businesses are attacked by hackers every single day. Yet despite this, only 32% of UK businesses identified an attack in the last six months. Cyber attacks haven’t slowed. They’ve become harder to detect. Which is why it’s more important now than ever to know the types of cyber attacks your business faces. That’s where our helpful introduction to cyber attacks comes in.
Types of cyber attack
Understanding that different types of cyber attacks come in many forms and have any number of goals is the first step. It’s important to recognise that cyber attacks will not always look the same.
Sometimes, the goal is a financial one, and other times hackers are driven by political motives. Some hackers are just ambitious people who want to see if they can do it. Others may just have some petty grievance with a company and want to cause them indirect pain.
Beyond the financial impact (that has grown 72% in the last 5 years to almost £10 million a year), cyber attacks can cost reputations, disrupt families and even cost lives. It is a $6 trillion a year industry that’s showing no signs of slowing down.
But there are ways to fight it. The InfoSec industry is booming in response to the global need and software is becoming more and more adept at tackling threats before they appear.
The biggest threat to companies, however, remains to be education (or more specifically, the lack of it). So, to help you out, here are the most common types of cyber attacks your business is likely to face.
Introduction to cyber attacks: a list of common types
- Denial of Service Attacks
- Malware
- MitM Attacks
- Phishing Attacks
- SQL Injection
“There are two types of companies: those that have been hacked, and those who don’t yet know they have been hacked.”
John Chambers, Former Cisco CEO
Type of cyber attack: A denial-of-service
A denial-of-service attack is designed to stop your networks from working. They can’t pull the plug on your systems, so instead they bombard them with requests and data.
For example, if you try to connect to your company server from your computer, a message is sent along your network, hits the server and the server responds. That message takes up a little bit of bandwidth. Bandwidth is like a pipe, as the analogy always goes.
Now imagine tens of thousands of messages being thrown down the pipe every second. The pipe gets blocked and the server is overwhelmed with messages. Anything you try and do just hits a backlog of requests and never reaches the server. That is a denial-of-service, or DoS, attack.
Attackers can also use multiple compromised devices to launch this attack. This is known as a distributed-denial-of-service (DDoS) attack.
How effective can these attacks be?
According to a 2017 report, by 2021, hackers will be able to send 1GB of data into your systems every second with ease.
In February 2018, GitHub, a popular developer platform, was hit with a DDoS attack that sent 1.35 terabits of data every second into their servers and systems.
According to GitHub, the traffic was traced back to “over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints.”
What’s worse is that GitHub was not entirely unprepared for a DDoS attack—they simply had no way of knowing that an attack of this scale could be launched.
Impact
The impact of a DoS attack can be hugely costly to your IT teams. Identifying a DoS attack can be challenging all on its own. Working out what’s going on requires sending requests to servers and networks, which can be slowed or blocked by the attack.
Once identified, you need to figure out how to block the spam traffic and allow normal service to resume. Eventually. You parse all the spam requests and those blocked pipes become free again.
The world’s biggest DDoS attack sent 1.35TB of data every second to the target system
Type of cyber attack: Malware
Malware is a blanket term for “malicious software”. This can include spyware, ransomware, viruses, and worms. In order to affect your business, malware needs an entry point. Most commonly, it is given an opening when someone on your network opens an unexpected email attachment. Other times, a hacker physically enters your site and uses a USB port to upload malware.
Once inside your system, malware can do some or all of the following:
- Block access to key components of your network
- Covertly obtain information by transmitting data out of your network
- Disrupt components and render your system inoperable
How effective are malware attacks?
The most popular type of malware attack is ransomware, which is also one of the most common types of cyber attack. While WannaCry and NotPetya have received a lot of media attention, another piece of ransomware has been doing damage for years. At its peak in early 2017, a ransomware known as Cerber accounted for 26% of all ransomware infections.
As we mentioned, cybercrime is a trillion dollar industry and Cerber is distributed as ransomware-as-a-service (RaaS). It has hit millions of users worldwide and even offers an affiliate program for cybercriminals.
Cerber targets users with an elaborate phishing campaign. Typically, the victim receives an email with an infected Microsoft Office document attached. Once opened, ransomware runs in the background, encrypting all your files. After the encryption, users will find ransom notes in encrypted folders and on their desktops.
Impact
Cerber usually demands $280 in Bitcoin. In might not seem like much, but there are 3 problems with paying ransom ware.
- Paying the ransom doesn’t guarantee recovery of your data
- Paying a ransom doesn’t protect you from future attacks
- Paying a ransom funds cybercrime at large
Being denied your data can be agonising, as the NHS knows all too well, but yielding to the demands will only cause issues in the future. While most malware can be detected by modern firewalls, those that get through require a phishing element. This demonstrates the need for a better human firewall and company-wide training in an introduction to cyber attacks and cybersecurity.
Type of cyber attack: man-in-the-middle
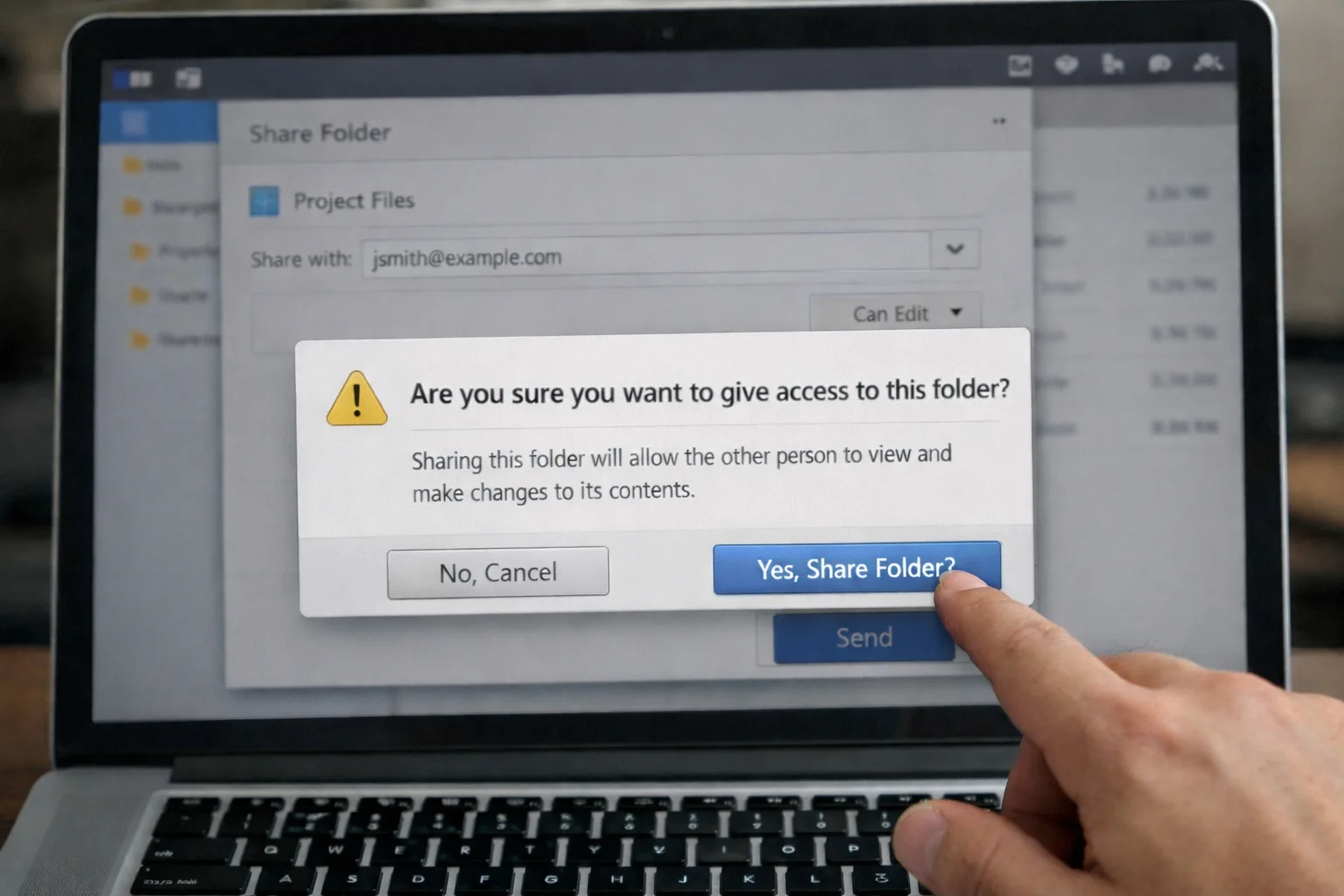
Man-in-the-middle (MitM) attacks, occur when attackers insert themselves into a data transaction. Between you and your online bank, for example. Once the attacker interrupts the traffic, they can filter and steal data.
Two common points of entry for MitM attacks:
- Malware is inserted into a device directly. The traffic is then monitored and harvested. More sophisticated versions can lay dormant for months, until a very valuable piece of data appears.
- On unsecure public Wi-Fi, attackers can insert themselves between your device and the network. Without knowing, you pass all information through the attacker, rather than the coffee shop Wi-Fi.
How effective are MitM attacks?
Due to their nature, MitM attacks are hard to track or spot. In a benign way, this technique was used during World War II after the Enigma Code was cracked. Codebreakers would intercept messages, decode them and pass them along, recoded.
There is one case of a couple who lost £340,000 after hackers intercepted their emails to their solicitors during a property sale.
Impact
MitM attacks are all about intelligence gathering. As such, they are commonly used today as part of more elaborate phishing scams and corporate espionage. The best versions of these attacks happen without you noticing. You aren’t even the intended target, but hackers will use your information to exploit someone else.
Type of cyber attack: Phishing
Phishing comes from the word “fishing” and deploys the same tactics. Using the right kind of bait, an unsuspecting target can be caught.
By exploiting ignorance and human psychology, phishing scams create a situation where you feel comfortable letting your guard down. Typically, you receive an email from a trusted source, such as your boss or your bank. That email will include a link or a request for information. If you fail to spot the artifice, your data is stolen or your computer is hacked upon clicking the link.
How effective are phishing scams?
Phishing attacks vary in their demands and many companies like to keep their attacks out of the public eye. But, one estimate suggests that this type of cyber attack averagely costs to a medium-sized company $1.6 million per attack.
Of the 124 billion emails sent every day, more than 1,000 of them contain a phishing scam. Your spam box is probably full of them right now.
Impact
These days, phishing scams are easy to spot, but people still fall for them every day. More sophisticated phishing scams target specific people, like CEOs and CFOs. This is called ‘Whaling’ because targeting a powerful and influential person with a scam can be far more lucrative.
This is why it is so important to make sure that even board members receive cyber security training.
1 in 25 branded emails… is a phishing email
Type of cyber attack: SQL injection
An attacker can force a server to reveal information you would rather have safe by injecting queries using Structured Query Language (SQL).
What this means is that if your website isn’t built properly, hackers can use any field on your site to input code and trick your server into giving them information. Usually, this causes your server to reveal all your customer data, including passwords, names and bank information.
Impact
SQL injections are getting harder and harder to pull off. Modern website builds and the introduction of SSL certification is helping to encrypt and protect businesses from being exploited by faulty form fields. SQL injections have led to the rise of field validation, giving IT teams more control over the information that users are putting into their websites.
How effective are SQL injections?
In October 2015, Talk Talk revealed that they were being extorted for the return of data stolen by hackers who had used an SQL injection. The attack, which was launched on a system that belonged to a company Talk Talk had just bought, allowed the hackers to burrow their way into the valuable customer records and hold the telecoms giant to ransom.
In addition to a £400,000 fine levied from the Information Commissioner’s Office, the company lost millions in reputation damage, employee hours and lost service.

When it comes to cyber attacks, knowledge is power
Not all cybercrime can be prevented with tech alone. Your people are your human firewall and you need to provide them with the skills and awareness to help keep your organisation safe.
The ramsac phishing awareness subscription is a great way of increasing awareness. We help you test which of your employees can spot a phishing email and which are fooled by them. Get in touch for more information.