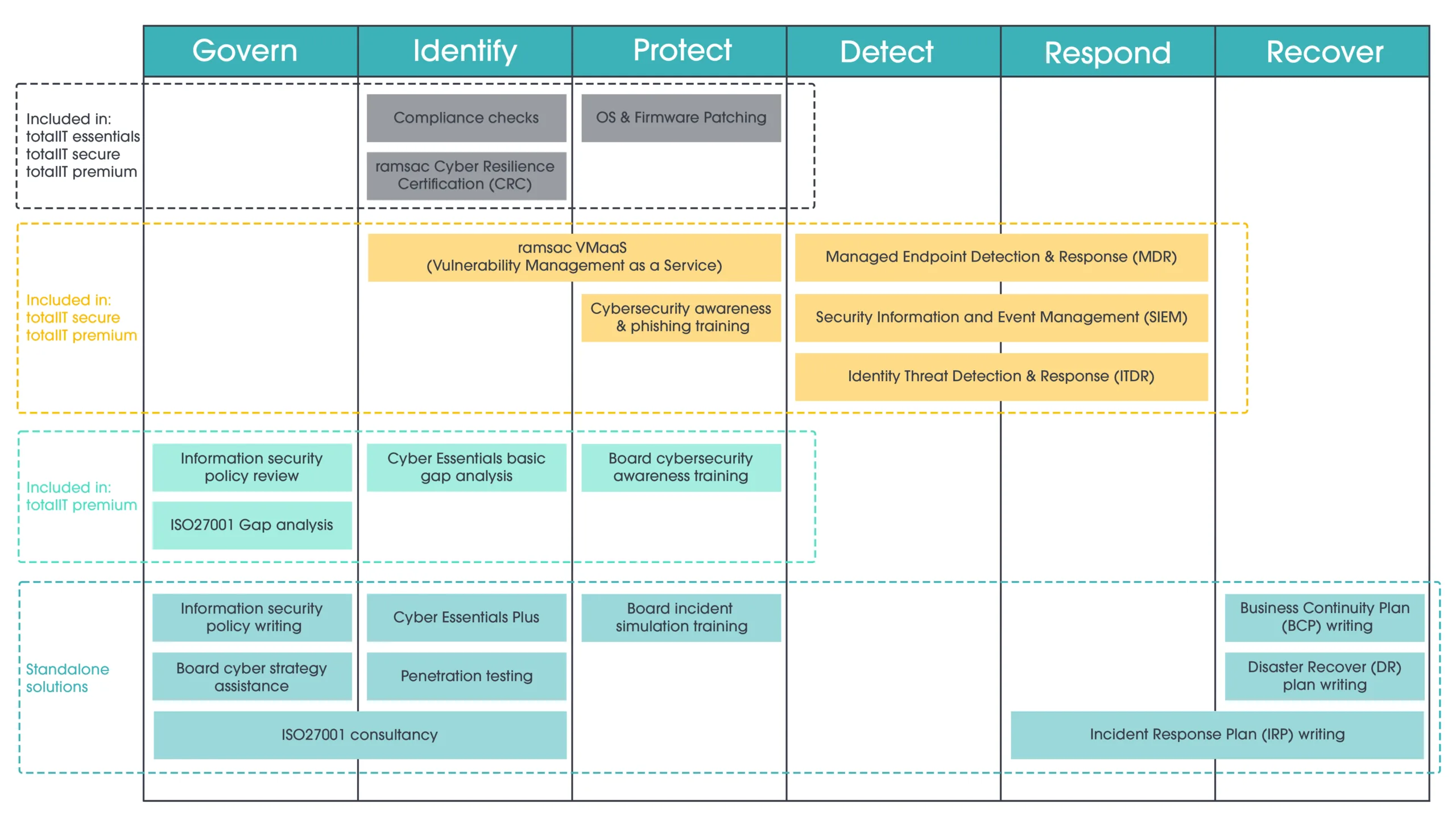
A Microsoft 365 (previously Office 365) password policy defines how users must create and manage their login credentials to enhance both computer and network security. These rules typically cover password length, complexity, banned passwords and additional identity requirements such as multi-factor authentication (MFA).
Microsoft has some baseline security policies of its own across its services, but administrators can customise these settings through the Microsoft Entra admin centre previously known as Azure Active Directory).
A carefully defined password policy encourages users to create, implement and use stronger passwords to protect your network and digital assets. It is a crucial tool in protecting against unauthorised access, phishing attempts and breaches of data, so it is important for administrators to align their settings with Microsoft’s recommendations and modern cybersecurity standards.
Password policies are usually covered in an organisation’s cybersecurity awareness training. Others may also choose to partner with a trusted Microsoft 365 consultancy to leverage the dynamic security benefits provided.
What should your Microsoft 365 password policy include?

When using Microsoft 365, an ideal password policy should include the following:
1. A minimum character count
The fewer the characters in a password, the easier it is to guess, and the more susceptible it is to a brute force attack that uses trial and error to crack passwords, login details, and encryption keys. You don’t need to set a 14-character minimum for every password, but it’s good to set a lower limit of characters for your company employees.
A 365 password policy requires a minimum of 8 characters, although Microsoft recommends at least 12 characters long, and 14 characters or more is better.
2. A ban on common passwords
Microsoft already has a list of passwords that are banned by default, but offers you, or your IT support company, the option to add additional words to a custom list. These can include your company name, and abbreviations of local place names, industry terms, or even in-jokes at the office.
These common passwords can be easily guessed by cyber criminals, so banning them is a good idea. It protects your company from the risk of a cyberattack, data breach, phishing scam, and other cybercrimes that could bring a business to its knees.
3. Multi-factor authentication (2FA and MFA)
Multi-factor authentication (MFA), and two-factor authentication (2FA), offer more security layers when approving logins and access to company systems and networks. Within Microsoft, you have many options, such as sending a text or email, or using the Microsoft Authenticator app for biometric security, such as fingerprint scanning or facial recognition. Enforcing MFA is a much more secure way to approach passwords and encourages ownership of cybersecurity.
Understanding Microsoft Intune
Visit our resources page to understand how Microsoft 365 can help you work, learn, organise, connect, and create.

What shouldn’t be in your 365 password policy?

While the above three examples are all fantastic things to have, we, and Microsoft, also have some important suggestions for what you shouldn’t include in your 365 password policy.
1. Password expirations
It’s been proven by America’s Federal Trade Commission (FTC) that periodic password changes do more harm than good.
Previously, Microsoft enforced password expirations and required these periodic changes. However, they have since changed their stance, as users often use weak, reusable passwords that criminals can exploit.
In the article, Lorrie Cranor, Chief Technologist at the FTC, states: “There is a lot of evidence to suggest that users who are required to change their passwords frequently select weaker passwords to begin with, and then change them in predictable ways that attackers can guess easily.”
For example, if you have a password that is water12, someone may make the next change water13, then water14 and so on. Expirations make it easier for a hacker to figure out the pattern and continually breach your system.
While Microsoft Azure AD still defaults to expiring passwords every 90 days, admins can change this setting if they so wish.
2. Using complex character requirements
Again, you may think that the more character requirements you have, the more secure a password will be. Microsoft states that forcing your users to choose a combination of upper, lower, digits and special characters has a negative effect, as common replacements such as $ for S or @ for A are easy for bad actors to guess.
Luckily, Microsoft 365 comes with default password complexity settings which organisations can adjust to align with their own security policies. In practice, this means your 365 password policy should include at least 3 of the following character types:
- Uppercase characters (A to Z)
- Lowercase characters (a to z)
- Numbers (0 to 9)
- Permitted symbols, such as @ ! # = { } % & / , < > . ;
- Password length of at least 8 characters, but ideally 12 or more
How to create a secure password policy in Microsoft 365
Creating a password policy in Microsoft 365 isn’t as simple as pressing a button, and there are many important steps to follow. We’ve broken down the core parts here, but if you want a professional’s help, please get in touch.
Go to the Microsoft 365 admin centre
Begin by signing in to the Microsoft 365 Admin Center[AS1] – the central hub for managing your organisation’s settings, including security and compliance.
Navigate to security & privacy
After accessing the Admin Centre, navigate to ‘Settings’ and choose ‘Security & Privacy’. This is where you’ll find a range of options to manage your organisation’s security policies.
Configure your 365 password policies
Inside the ‘Security & Privacy’ settings, you can adjust your organisation’s password policies. Key areas to review include:
- Password length: Set a minimum length. Microsoft requires a minimum of 8 characters, though at least 12 is recommended for stronger protection.
- Complexity rules: Require a mix of uppercase and lowercase letters, numbers and special characters.
- Password expiration: Decide how often users must update their passwords. 90 days is a common standard.
- Password history: Stop users reusing old passwords. Saving the last 24 as a reference is good practice.
- Account lockout: Set limits for failed login attempts and define lockout durations to help block brute-force attacks.
Enable multi-factor authentication (MFA)
Multi-Factor Authentication (MFA) strengthens account security by requiring users to confirm their identity through two or more verification methods. For example, this could involve something the user knows (like a password) and something they have (such as a mobile device to receive a verification code).
To enforce MFA in Microsoft 365, you need to be a global admin. Then you need to:
- Go to the Microsoft 365 Admin Center.
- Select ‘Show All’, then choose the Microsoft Entra Admin Center.
- Select ‘Microsoft Entra ID’, then ‘Properties’, and then ‘Manage Security defaults’.
- Under Enable Security defaults, select ‘Yes’ and then ‘Save’.
Educate and train your users
A strong Microsoft 365 password policy only works if employees follow it. To ensure your workforce complies, run regular cybersecurity training sessions to educate staff about the importance of strong password protocols and highlight the risks of poor practices, like writing password down or sharing them with colleagues.
Continuously review and refresh policies
Since cyber threats are continually evolving, your password policies should adapt too. Regularly assess and update them to stay aligned with current security best practices for maximum cyber protection.
How to add custom banned passwords in Microsoft 365
Adding custom banned passwords in Microsoft 365 isn’t overly simple, but before you begin, you’ll need to be a global admin, and have the list of banned passwords ready, with each banned word on a separate line.
- Sign in to the Microsoft Entra Admin Center as at least an Authentication Policy Administrator.
- Browse to Protection > Authentication methods, then Password protection.
- Set the option for Enforce custom list to ‘Yes’.
- Add strings to the custom banned password list, one string per line. The following considerations and limitations apply to the custom banned password list:
- The custom banned password list can contain up to 1,000 terms.
- The custom banned password list is case-insensitive.
- The custom banned password list considers common character substitutions, such as “o” and “0”, or “a” and “@”.
- The minimum string length is four characters, and the maximum is 16 characters.
- Specify your own custom passwords to ban.
- Modify the custom banned password list under Authentication Methods.
- Leave the option for Enable Password Protection on Windows Server Active Directory to ‘No’.
- To enable both custom banned passwords and your entries, press ‘Save’.
It may take several hours for updates to the custom banned password list to be applied so carefully consider when you do it. For instance, running updates in the middle of the day could harm workflow and lead to disruptive downtime, whereas doing this during non-working hours is likely to cause less of a disturbance.
Can you replace Microsoft passwords with passkeys?
Yes, Microsoft has introduced innovative advancements in the adoption of passkeys as it moves towards a passwordless future. These user-friendly alternatives to traditional passwords deliver enhanced security measures for added protection. Passkeys not only streamline user experience, but they mark the beginning of a new era in digital authentication.
Given that Microsoft confirmed it blocked 7,000 password attacks per second in the past year, it is constantly devising new ways to strengthen security policies. By implementing passkeys, businesses can reduce the risk of password-related cyber attacks while improving regulatory compliance.
Passkeys offer a cutting-edge approach and a smoother user experience by enabling fast sign-ins with your face, fingerprint, or PIN. Unlike traditional passwords, they are resistant to common attack methods, making them a far more secure alternative.
Are you looking for support with creating a secure password policy?
Here at ramsac, we work with companies to create more secure login systems and improve their cybersecurity. We can help your business improve its password security.