
IT Blog

Power BI Free vs Pro vs Premium: Which do you need?
Power BI offers exceptional data tools to users, but which license should you choose? Find out more in our blog. [...]

What is a break glass account?
If you’re creating a business continuity plan, have you considered a break glass account? Learn what one is and how to create one here. [...]

Microsoft Copilot vs Bing Chat: Understanding Microsoft and AI
Microsoft are gearing up to release Microsoft Copilot which is a suite of AI Powered tools. In this blog post, we explain what you need to know about Microsoft [...]

ramsac wins double awards at Surrey Business Awards 2023
ramsac celebrates winning two awards at the Surrey Business Awards 2023, Employer of the Year and Large Business of the Year [...]

Cybersecurity vs cyber resilience – what is the difference?
What’s the difference between cybersecurity and cyber resilience, and how can you implement them? We cover this and more. [...]
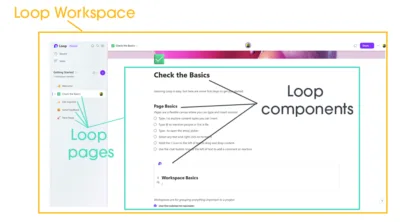
Microsoft loop: A new way to collaborate
Microsoft describe Microsoft Loop as a transformative co-creation experience, in this blog we look at what that means and how Loop can help us collaborate more effectively. [...]

Scheduling Poll vs FindTime
FindTime is now called Scheduling Poll. Discover what Scheduling Poll is, how to use it and how it differs from FindTime. We explore it here. [...]

Why the cybersecurity industry needs more women
Cybersecurity is a vital and growing field that needs more women to join its ranks. In this blog, we explain why the cybersecurity industry needs more women and how [...]

ramsac shortlisted for two Surrey Business Awards 2023
We have been nominated for two prestigious awards at the Surrey Business Awards 2023, which celebrate the best of the best in the county. Read our blog to find [...]

