
IT Blog

Removing the Dell Driver vulnerability
We have compiled simple to follow instructions for how to download Dell’s security update tool that will detect and automatically remove the vulnerability from your machine. [...]

How secure is your data? A guide to data backup and disaster recovery
Discover how secure your business’ data is and how data backup and disaster recovery can mitigate the impact of data loss with ramsac’s helpful guide. [...]

When is it time to upgrade your computer?
When is the best time to upgrade your computer? Get support and advice for the best times to upgrade, or learn the signs that your computer needs replacing... [...]

Social distancing in offices – IT considerations
A practical look at the IT considerations that need to be thought about over the coming weeks when planning the reopening of your office. [...]

How to: Live Meeting Transcription in Microsoft 365 Teams
We have created a short video to demo Microsoft 365 Teams' new feature, Transcription, using this feature, Teams can record who said what, when and produce an on the [...]

How organisations should react to zero-day threats
A zero-day threat is an attack that exploits a potentially serious software security weakness that the vendor or software developer may be unaware of. This blog explains what it [...]
A guide to Microsoft MyAnalytics (now Viva Insights)
From wellbeing to productivity, find out how Microsoft’s business analytics tool, MyAnalytics, can help to better manage team workloads. Find out more here. [...]
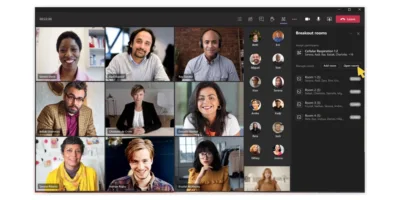
How to set up Microsoft Teams breakout rooms
Microsoft Teams is constantly evolving, as Microsoft develops new features to improve its collaboration capabilities. A significant new feature allows users to set up 'breakout rooms' during meetings. In [...]

A guide to UK cybercrime legislation + helpful links
Cybercrime is everywhere online. As well as this, cyber-risks are increasingly harder to identify as cyber-crime becomes more sophisticated and harder to identify. With threats posed by everything from [...]
