When building cyber resilience within an organisation there is no end point, cyber risks are constantly evolving and organisations need to continually adapt to new challenges and threats. Microsoft 365 is helping organisations to not only work smarter but also safer. Microsoft 365 includes popular apps like Word, Excel, PowerPoint, Outlook, and Teams, as well as advanced security features that protect your data and devices from cyberthreats. The key to this additional security is Microsoft Intune, a cloud-based platform for controlling user access and device management. Microsoft is constantly evolving and improving its security offerings to meet the changing needs and challenges of the modern workplace. In this blog post, we will explain some of the key security acronyms that you may be encountering at work, such as MFA, MDM, MAM, DLP, and Conditional Access. We will also give you some examples of how these tools can help you defend against various cybersecurity risks.
MFA: Multi-factor authentication.
MFA is a method of verifying your identity when you sign into an online service or app. It requires you to provide at least two pieces of evidence, such as a password and a code sent to your phone, to prove that you are who you say you are. MFA can defend against cyberattacks that try to steal your credentials or hack into your accounts. For example, if you want to access your email account from a new device, you may be asked to enter your password and a code that is sent to your phone or email. This way, even if someone knows your password, they won’t be able to sign in without the code. MFA can prevent against phishing and brute force attacks that try to guess or steal your password.
MDM: Mobile device management.
MDM is a way of managing and securing the entire mobile device, not just the apps. It allows you to enrol, configure, monitor, and wipe the device remotely. MDM can defend against cyberattacks that try to compromise or steal your device or its data. For example, if you lose your work device or it gets stolen, you can use MDM to remotely lock or wipe the device. You can also use MDM to enforce security settings on the device, such as requiring a password, updating the software, or encrypting the data. This way, you can protect your device and its data from being accessed or used by someone else. MDM can prevent device theft, data loss, and device tampering that may expose your device or its data to risk.
MAM: Mobile application management.
MAM is a way of controlling and securing the apps that you use on your mobile devices, such as smartphones and tablets. It allows you to apply policies and settings to the apps, such as requiring a PIN or encrypting the data. MAM can defend against cyberattacks that try to access or tamper with your data or apps on your mobile devices. For example, if you use a work app on your personal device, you may be required to enter a PIN or use biometric authentication to open the app. You may also be restricted from copying or saving data from the app to other locations. This way, you can keep your work data secure and separate from your personal data. MAM can prevent unauthorised access, and malware infection that may compromise your work data or apps.
DLP: Data loss prevention.
DLP is a way of preventing your sensitive or confidential data from being leaked, copied, or shared without your permission. It allows you to classify and protect your data based on its content and context. DLP can defend against cyberattacks that try to exfiltrate or expose your data, either intentionally or accidentally. For example, if you have a document that contains sensitive information, such as customer data or financial reports, you can use DLP to label the document as confidential. You can also use DLP to apply protection to the document, such as preventing it from being printed or shared with unauthorised people. This way, you can ensure that your data is handled according to your policies and regulations. DLP can prevent data breach, data misuse, and data non-compliance that may result in legal or reputational damage.
Conditional Access.
Conditional Access is a way of enforcing rules and conditions that determine who can access what, when, where, and how. It allows you to set up policies that evaluate the risk level of the user, device, app, and location before granting or denying access to your resources. Conditional Access can defend against cyberattacks that try to bypass your security controls or exploit your vulnerabilities. For example, if you want to access a cloud app from your device, you may be subject to certain conditions, such as the device being compliant, the location being trusted, or the app being approved. If you don’t meet the conditions, you may be blocked or challenged to verify your identity or provide additional information. This way, you can reduce the risk of granting access to untrusted or compromised users, devices, apps, or locations. Conditional Access can prevent unauthorised access, identity theft, and malicious activity that may harm your resources or services.
Microsoft 365 security solutions leverage AI and cloud intelligence to detect and respond to emerging threats, automate security workflows, and empower users with self-service options. They are a comprehensive suite of tools to secure your data and devices in the modern workplace. However, these tools are not automatically configured or deployed, and they require careful planning and management to ensure optimal performance and protection. That’s why ramsac is here to help you with your Microsoft 365 security journey. We can help you assess your current security posture, implement the best practices and policies, and provide ongoing support and training. If you want to learn more about how Microsoft 365 and Intune solutions can help your organisation be more efficient and secure, please download our brochure.

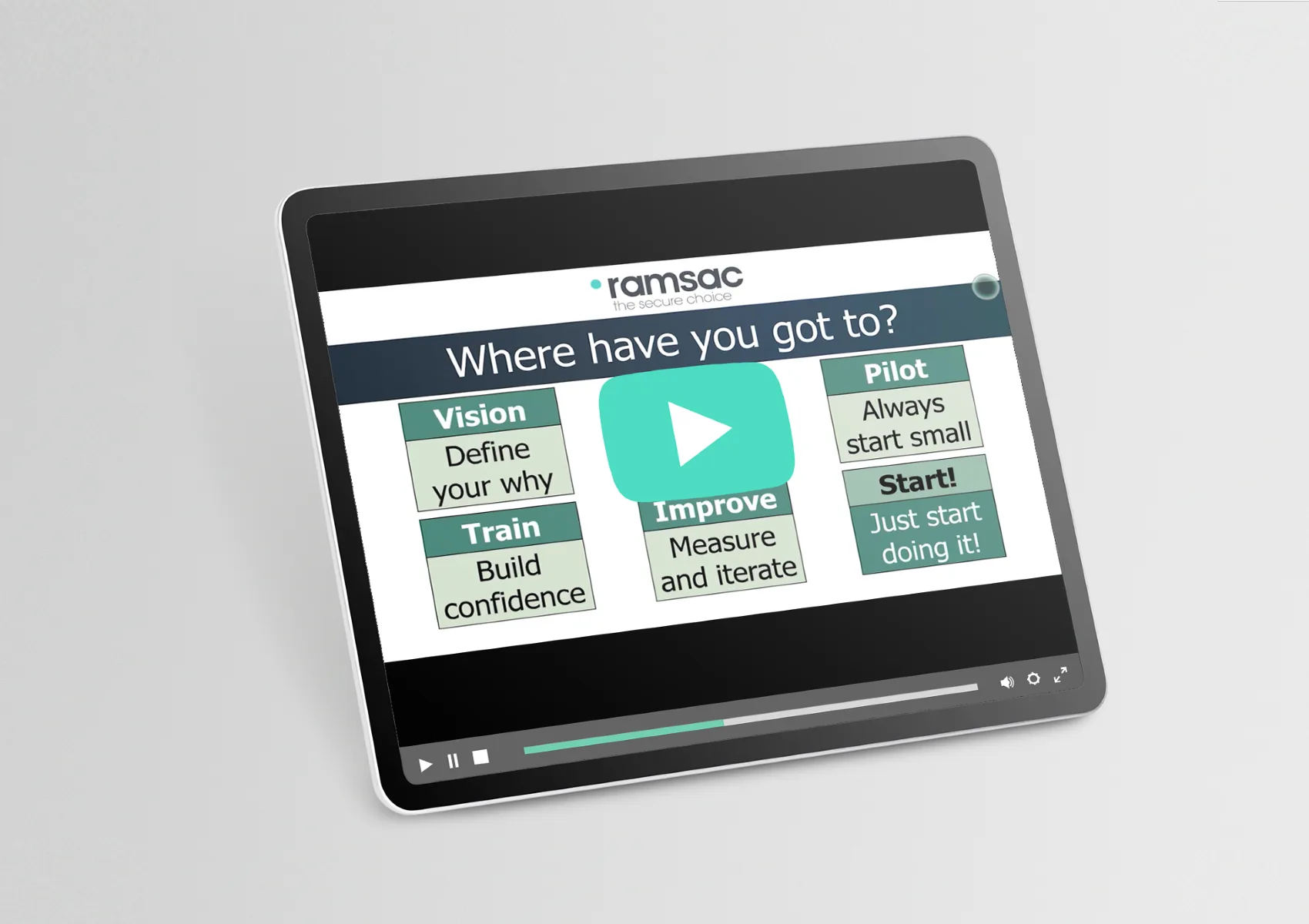
Where are you on your 365 security journey?
We have created a whitepaper that covers all you need to know about the Microsoft 365 security journey, that will help you identify where your organisation is on that journey and how to protect your data.