Many organisations assume that cybersecurity is all about stopping viruses and hackers, but often overlook one of the most common entry points for attackers: known software vulnerabilities. Cyber threats are growing in volume and complexity. Yet many business leaders still believe cybersecurity is something only the IT department needs to worry about. The truth is, protecting your organisation from cyber risks is a shared responsibility, especially when those risks come from known vulnerabilities that could have been prevented.
This is where vulnerability management comes in.
Think of vulnerability management like maintaining the locks and alarms on your building. It’s not enough to install security once and forget about it. You need to regularly check, reinforce, and upgrade your defences because burglars, like cybercriminals, constantly find new ways to break in. Just as you wouldn’t ignore a broken window or a faulty alarm, you can’t afford to ignore known weaknesses in your IT systems.
Understanding Vulnerability Management
Vulnerability management is the process of identifying, assessing, and resolving weaknesses in your IT systems that could be exploited by cybercriminals. These weaknesses, called vulnerabilities, are often caused by outdated software, misconfigured systems, or known bugs in widely used applications.
Crucially, vulnerability management is not a one-off task. It’s a continuous, proactive process that helps ensure your business stays ahead of evolving threats.

What does the process involve?
At a high level, vulnerability management includes several key steps:
- Discovery 🔍 – This is the starting point where automated tools are used to scan your network, devices, and applications to detect known vulnerabilities. It helps create an inventory of assets and highlights where weaknesses exist.
- Assessment 📝 – Each identified vulnerability is analysed to understand how severe it is, how likely it is to be exploited, and what impact it could have on your business. This step often involves matching the vulnerabilities against threat intelligence feeds.
- Prioritisation 📊 – Not all vulnerabilities pose the same level of risk. Here, issues are ranked based on urgency and potential impact, so your team can focus on what matters most—protecting critical systems and sensitive data.
- Remediation 🛠️ – This involves taking appropriate action to fix the vulnerabilities. That might mean applying patches, changing configurations, updating software, or even retiring outdated systems.
- Reporting 📄 – Good reporting provides a clear record of identified vulnerabilities, the actions taken, and their current status. This helps track progress, satisfy compliance requirements, and inform future risk decisions.
This might sound complex, but when managed properly, it becomes a critical part of your organisation’s cybersecurity posture.
Why SMEs struggle with Vulnerability Management
Small and mid-sized organisations often face unique challenges when it comes to cybersecurity. Limited IT resources and a lack of in-house expertise can make it difficult to stay on top of every patch or system update. Meanwhile, the threat landscape continues to grow,with attackers actively scanning for known vulnerabilities that have yet to be fixed.
Common roadblocks include:
- Not knowing what systems are vulnerable or how to assess risk
- Infrequent or inconsistent patching
- Limited visibility across the entire IT environment
- Compliance pressures, especially for regulated sectors like Finance and Not-for-Profit
In this context, it’s easy to see how vulnerabilities can go unnoticed, until it’s too late.
The business risk of ignoring vulnerabilities
Cybercriminals aren’t always looking for sophisticated ways to breach your defences. In many cases, they’re simply exploiting known, unpatched vulnerabilities that are freely available in public databases. A breach caused by such an oversight can lead to data loss, reputational damage, financial penalties, and significant downtime.
For example, an unpatched vulnerability in a firewall or remote access tool could give attackers a foothold into your systems. And because these weaknesses are often discovered only after an incident, the damage can already be done.
Vulnerability management is about removing those easy targets and giving attackers fewer opportunities.
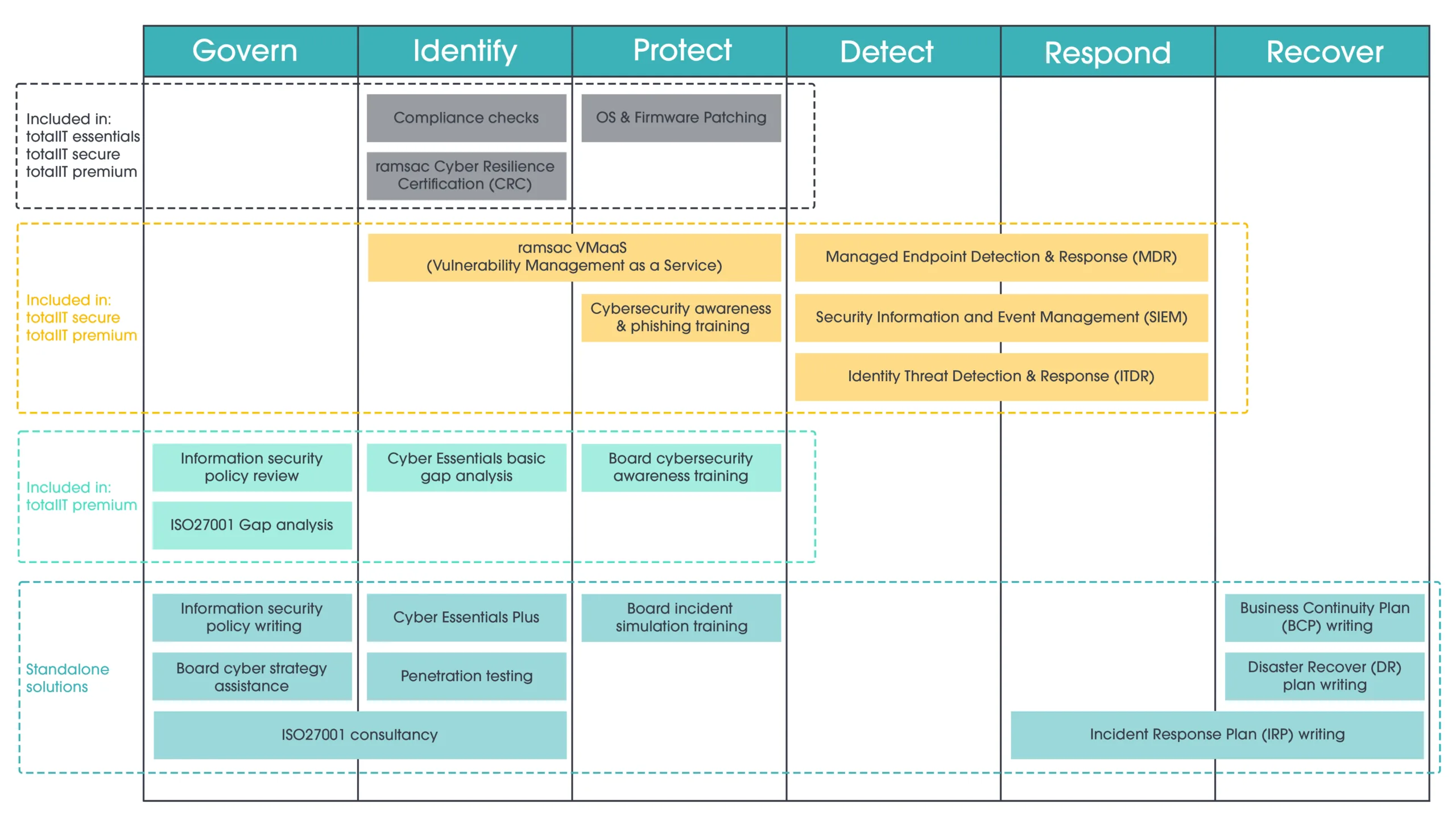
How ramsac’s VMaaS can help
That’s where our Vulnerability Management as a Service (VMaaS) comes in.
ramsac’s VMaaS is a fully managed service that continuously scans your IT environment for software vulnerabilities and provides you with clear, prioritised reporting. Our experts interpret the findings, recommend the most effective actions, and help you address software-related issues swiftly, before they’re exploited.
Unlike traditional annual scans or audits, VMaaS delivers ongoing protection and peace of mind. We take care of the technical heavy lifting, focusing on identifying and managing vulnerabilities in operating systems and applications, while you retain visibility and control.
With VMaaS, you benefit from:
- Regular vulnerability scanning across your systems
- Actionable insights that prioritise real business risks
- Expert advice tailored to your organisation
- Simplified compliance reporting

Most importantly, you’re not just finding problems, you’re fixing them, with our team right alongside you.
Take proactive control of cyber risk
Cybersecurity doesn’t have to be overwhelming. Much like securing a physical building, it’s not just about having locks in place, it’s about making sure they’re still working, that the alarm system is up to date, and that any weaknesses are addressed before they become entry points. Vulnerability management plays that exact role in your digital environment, helping you stay one step ahead of cyber threats.
By taking a proactive approach, you’re strengthening your organisation’s defences, reducing the chance of a disruptive incident, and making it significantly harder for attackers to find a way in.
If you don’t have the time, tools, or in-house expertise to stay on top of vulnerabilities, we’re here to help.
👉 Find out more about how ramsac’s VMaaS solution can protect your business.
What is VMaaS and why does your organisation need it?
VMaaS stands for “Vulnerability Management as a Service” and is ramsac’s service offering to help safeguard your organisation from software vulnerabilities.
We use a state-of-the-art tool to identify vulnerabilities across your workstations and servers, automatically update or patch software from a large catalogue of supported software, and proactively work to reduce the overall number of vulnerabilities across your devices that could be exploited by cyber criminals.