How to stay protected against COVID-19 scams

Posted on April 2, 2020 by Louise Howland
Cybercriminals are unscrupulous people who will capitalise on anything to extort money from individuals and organisations. The current Covid-19 (coronavirus) pandemic is no exception. Since the early days of the virus, we’ve seen hackers exploiting people’s fears by sending phishing emails and messages related to the Coronavirus. And at a time when many organisations have taken their eye off the importance of IT security to focus on their immediate response to the UK lock down, the impact of these attacks has been greater than ever. In this blog, we explore some of the latest coronavirus cybersecurity scams that are currently circulating.
The WHO Scam

Cybercriminals have started posing as the World Health Organisation to steal money and information from the public. The attacks range from fake landing pages, downloads and malicious email attachments all relating to the coronavirus outbreak.
In a recent press release, the WHO said: “If you are contacted by a person or an organisation that appears to be from WHO, verify their authenticity before responding”.
HMRC text message
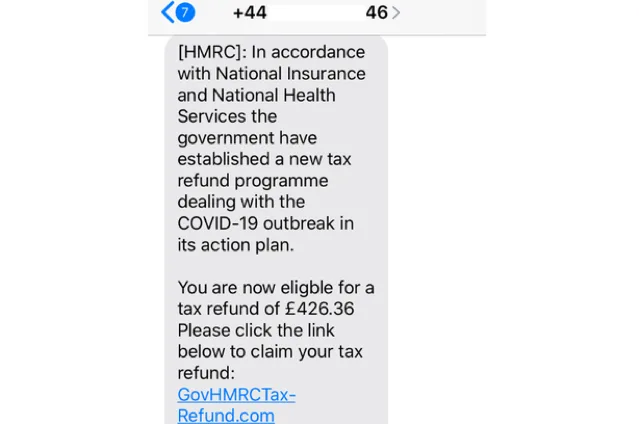
Almost as soon as the Government had announced greater support from HMRC, we started to see text messages supposedly from HMRC, promising a goodwill tax refund if recipients just follow the link.
On closer inspection, there are grammar mistakes in the text, and HMRC has confirmed that they would never text you a link for claiming a tax refund. If you look closely, you’ll see that the link does not look like a legitimate link to HMRC or gov.uk which is a classic sign that an offer is too good to be true. If you are unsure about any text messages, you receive you should always call the company to call to verify the legitimacy of the message.
City Council text message
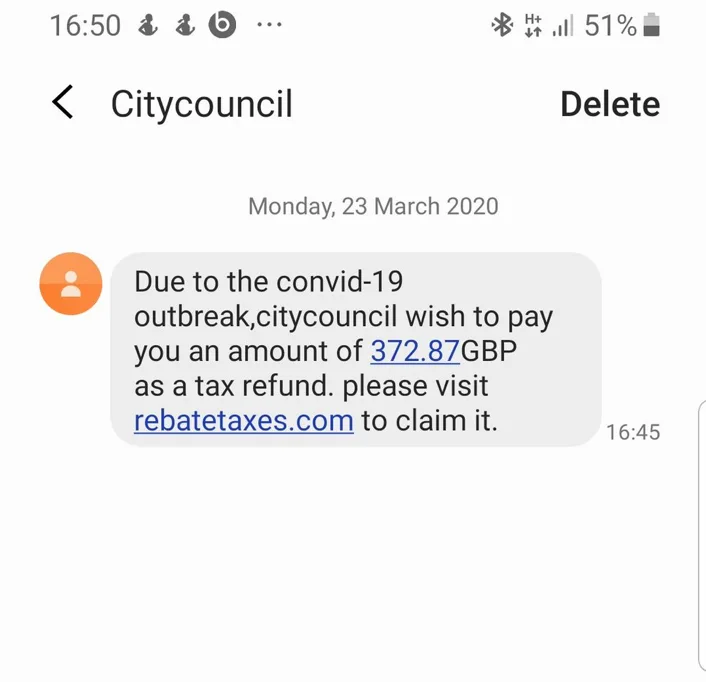
This example of smishing (a form of phishing where someone tries to trick you into giving them your private information via a text or SMS message), is this text supposedly from the ‘City Council’ again stating that they want to give you a tax refund. Note that they have even managed to spell Covid-19 wrong! often poor grammar in the message is a clue – but these are desperate times and people have been falling for this message.
UK GOV website
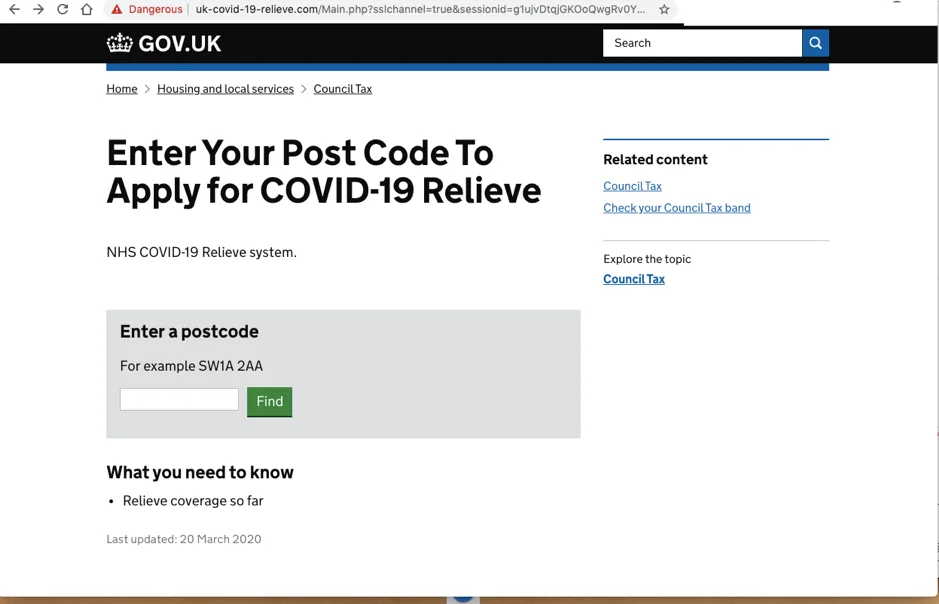
The Gov.uk website has been realistically copied in order to lure people into sharing personal information, in this example, the website looks similar to the gov.uk site, however, the URL does not look legitimate. The poor spelling also points to the fact that this is a fraudulent website, note they have called it the COVID-19 Relieve scheme instead of COVID-19 Relief scheme.
GOV UK Email
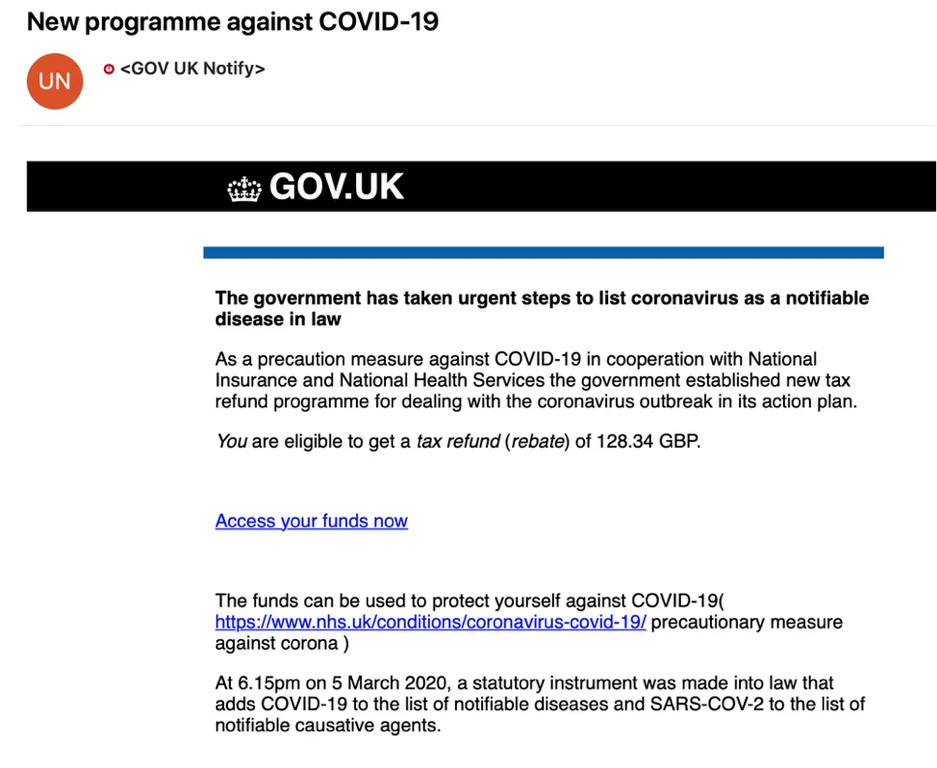
And on a similar theme, we’ve also seen this email, claiming that the Government has taken action to provide people with a tax refund. This imitated GOV UK with the email design and also had links for the recipients to click on to “Access their funds”.
We’ve said it before – but this just isn’t how the Government would proceed – they wouldn’t ever make it that simple! Remember, if it looks too good to be true – it probably is!
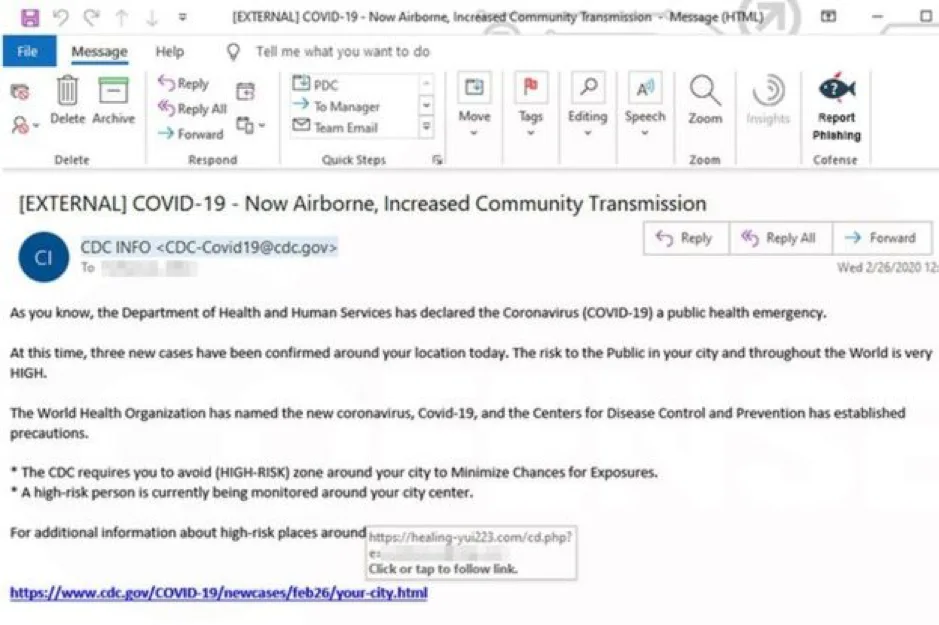
In the example above (source: Cofense) the email is directly impacting people’s fears by giving false information on the current pandemic by suggesting that the virus is airborne. This email has been created by using the legitimate Centres of Disease Control (CDC) emails but it has been sent using a spoofing tool. By sending an email of this kind during a period of such high stress and uncertainty, cybercriminals are capitalising on people’s fears to trick them into giving out their details.
Microsoft Teams
Recently there have been reports of phishing scams through Microsoft Teams. According to Tech radar, criminals are using fake Microsoft Teams alerts to try and gain Office 365 access to compromise peoples accounts. If the user clicks on the link via a fake Teams alert, it takes the user to an imposter landing page which will ask for personal details and can result in a data breach. There has generally been an increase of hacks through video conferencing channels due to the rise of users during the coronavirus pandemic.
It is vital that people are taught how to spot the signs of a phishing text, email or website, to protect themselves and the organisation they work for.
The UK government has recently been working with various social media firms to help to stop the spread of fake news and dangerous content, and they will shortly be re-launching their ‘Don’t feed the beast’ campaign to help the public think about the content that they are sharing on the internet. More information can be found here on the HM Government website.
The key message here is to be extra vigilant when reading emails and text messages related to the Coronavirus. Many hackers are currently exploiting people’s nervousness through phishing attacks. Many employers have taken their eye off the ball when it comes to cybersecurity as they have taken a ‘do whatever it takes’ approach to getting their people set up to work from home. This is not the time to cut back on your security services, and indeed, perhaps this is the perfect time to get your staff to spend some extra time on cyber awareness training. Do get in touch if you want some ideas on how to best do this.

For more information on how to spot phishing messages take a look at our cyber chat video on phishing or our blog on phishing emails.







