Multi-factor authentication: why you should be using it and how to implement it
Posted on January 22, 2019 by Louise Howland
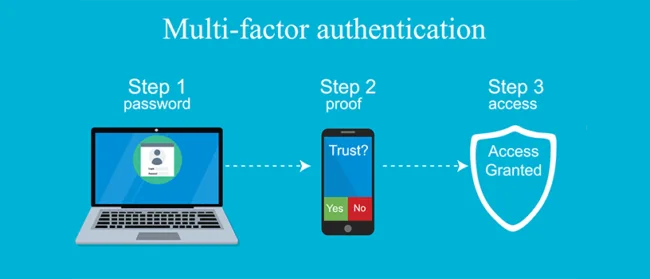
What is multi-factor authentication (MFA)?
Multi-Factor Authentication (MFA) is something everyone will have experienced. It’s the additional levels of security used when you sign into a banking app when you try to change a password and a verification code is sent to your mobile phone, or when you are asked to answer additional security questions after already providing your password. All of these examples are multi-step authentications that allow you to prove you are who you say you are. This provides peace of mind to both you and to the company providing the service that hackers can’t impersonate you.
Up until recently, especially with GPDR and similar data protection laws, most organisations have not considered implementing this additional layer of protection into their corporate data. With Office 365, it’s now a realistic, cost-effective option to improve the protection of your business data as flexible working becomes commonplace.
Why use MFA?
Obviously, the main reason for using MFA is security, if it is set-up correctly, it eliminates the risk of an account being compromised because of a weak, shared or known password. Increasing numbers of accounts (including Office 365) are being compromised, because users have used the same password across different systems. Services, such as LinkedIn and Adobe, have previously had their account databases stolen, giving hackers the ability to hack users’ accounts using the same credentials.
With MFA, even if someone knows your username and password, they are not able to log-in without access to your mobile phone or additional authentication device.
MFA user experience in Office 365
When it comes to setting up MFA in Office 365, one of the biggest barriers is end– user adoption. Fortunately, ramsac can help with the MFA setting up process as part of our Office 365 service. , but if you’re unsure about how your employees or customers may find it, have a read on to find out more about how it looks.
It is possible to set-up MFA to not to be required when logging in from a trusted network, so users won’t become frustrated by having to provide additional authentication when in the office or on a secure device.
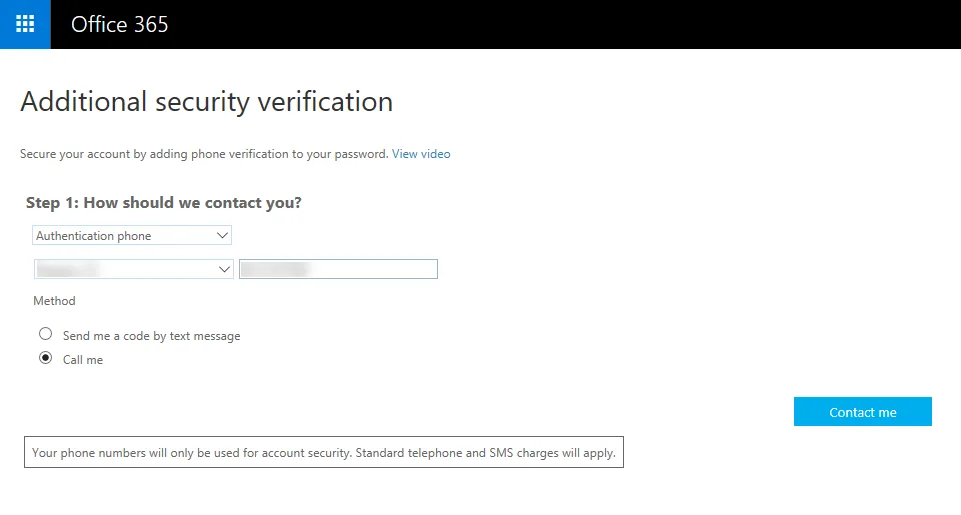
Choosing the security verification method in Office 365
When out of the office, a user can log in as normal using their username and password. If they are using an authenticator app on a mobile device, such as Google Authenticator, they get prompted to approve the login. This is by far the least intrusive and easiest option, not only to set up but to use regularly.
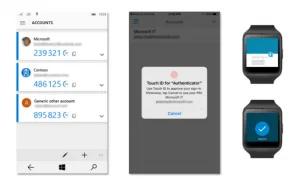
Using an authenticator app
If they click ‘approve’ they are logged straight in. Other options are using a code from the authenticator app, being sent a code by text, or a phone call with a recorded message giving a code. Overall, the experience is painless, and easy to understand, even for those who may struggle with technology.


Cybersecurity threats facing UK SMEs in 2025

Implementing multi-factor authentication and the risk factors.
Introducing MFA must be planned as a project as it’s potentially disruptive to end-users and could leave them unable to work. The risks organisations need to consider prior to implementing MFA, to ensure a smooth implementation experience are
- End-users may not get the correct authentication methods set-up, leaving them with a poor experience.
- End-users may forget some apps or devices and have issues at a later stage.
- Significant risk of end-users not being able to work across multiple applications if they are not given proper support and guidance during the implementation
When implementing MFA for organisations we follow several golden rules.
- Identify any applications that may integrate with Office 365, as those integrations may require an app password and will fail when MFA is enabled.
- Carry out an initial trial with just one or two users, so the trial can be paused quickly if any issues arise, so they can be quickly resolved
- After the initial trial, implement gradually throughout the organisation to minimise disruption if issues are uncovered.
- Provide plenty of support to each user to ensure they are confident in how MFA works and have a positive user experience.
Protect your organisation from Cybercrime.
IT systems are under attack on a daily basis, from a huge variety of cybersecurity threats, speak to us and we can help keep you secure.








